Online store SSG systems
Privacy out of the box for everyone
Our products will ensure the privacy and security of your personal information using modern technologies.
No more concerning your data may fall into bad actors' hands.
No more concerning your data may fall into bad actors' hands.
We guarantee the protection of your privacy

We only hire specialists with experience in the field of obtaining personal data. Each of our employees has knowledge of hacking, therefore knows how to protect against it.
Each product is tested first by individual employees, then by the team. We sell only products that have been fully tested on various levels.
Products

Kryptos Private Modem 4G Wi-Fi
Built-in VPN and Firewall will ensure privacy out of the box...
600 USD

Kryptos Private Laptop
Hardware-level protection against unauthorized hacking ...
4000 USD
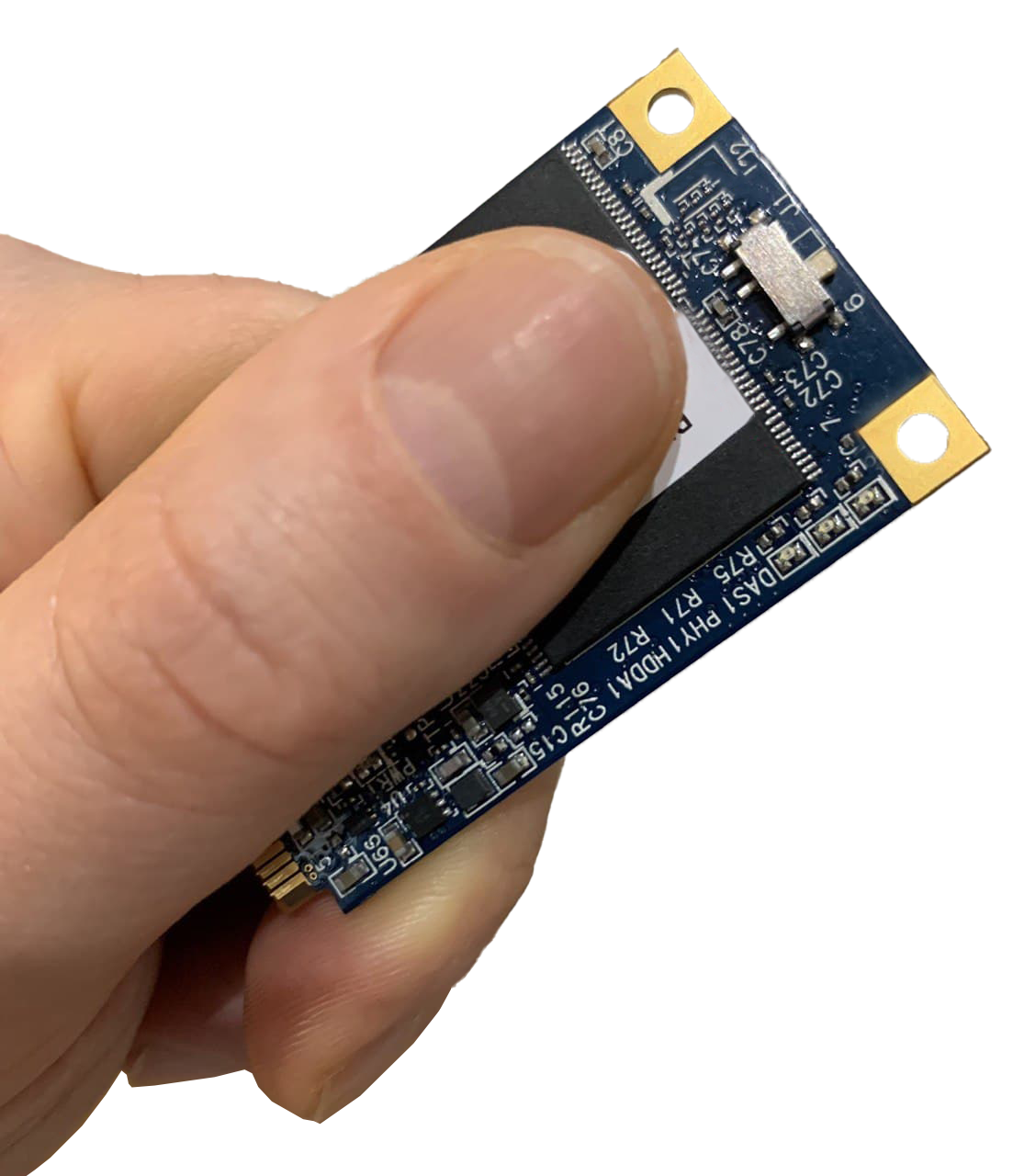
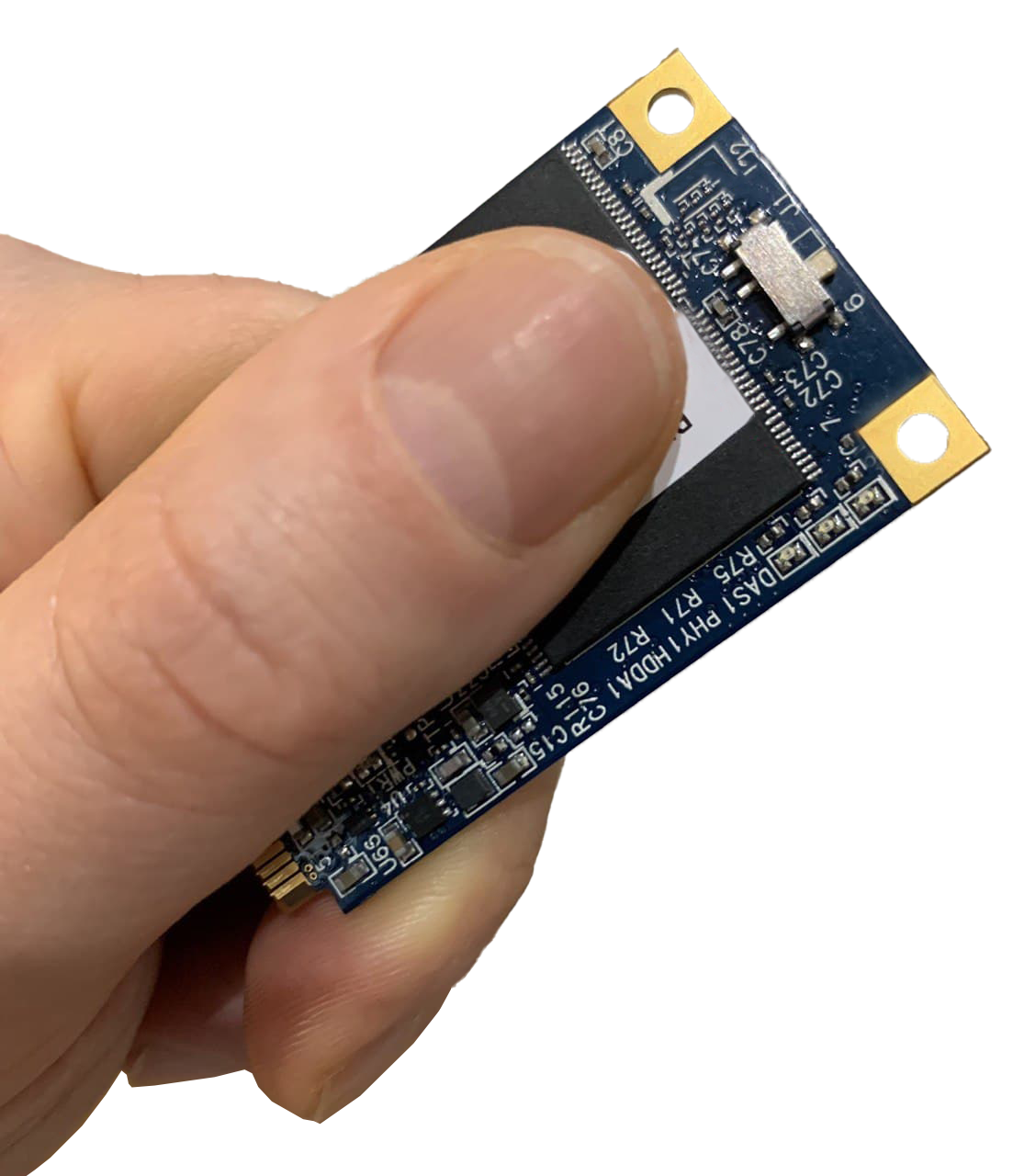
Kryptos Private Flash
Out-of-the-box protection against hacker attacks and industrial espionage ...
1500 USD



Anti-peeping glass/film
Protect the contents of your smartphone screen from prying eyes
50 USD

1000 USD
A tool for anonymity in the digital space.
RED PHONE



1000 USD
A tool for anonymity in the digital space.
BLUE PHONE



1000 USD
A tool for anonymity in the digital space.
GREEN PHONE

Ready solutions
Products you can use right now to secure your data



Kryptos Private Messenger
The Fondom Project
SSG Encrypted Messages





Services
We not only sell goods, but we also provide services to protect your data

Cyber hygiene training
The training system, developed by, us allows to expand on the necessary knowledge, skills, and competencies for the client and apply them effectively in practice.


Company's cyber security processes audit
Comprehensive company security assessment, scanning, and penetration testing, "shadow" IT audit.

Testing for company penetration

Authorized simulated hacker attacks on information systems, business processes, applications, and their business logic, and also on the staff.

Benefits of working with us
Convenient payment and shipping system
We deliver our products worldwide and have a wide range of convenient payment options, including crypto-currency.
Each product testing
Before we sell a product, it undergoes several stages of testing. And only after we are convinced of the complete safety of the product; we can offer it to you.
Best service
Individual approach to each client. Moreover, we have experience in digital and mobile forensics and cybercrime investigations.
How we work
Product order
Select the right product on the website and place your order. If necessary, we will answer any questions regarding the product. We send products only on 100% prepayment.

Payment
Pay for the goods in any convenient way for you. We will answer any question about payment methods and help you select the most suitable for you. When you order the goods — provide your address data, where you would like to receive the products, and what shipping method you prefer. The carrier we work with is Nova Poshta.

Choosing shipping procedure

When ordering, please specify in what city you would like to receive the product and which shipping method would be preferable. The shipping costs are calculated individually based on the procedure and country of delivery.

Receipt of products
The purchase is insured for their full value when they are shipped. Upon receipt, always inspect the item for damage in the operator’s presence. In the event of damage, the delivery service has to compensate the full cost of the item.

Exchange and return
You may exchange or return goods within 14 days of purchase. "Consumer Rights Protection Law" guarantees this right to you.
In order to use the exchange, and returning proper quality goods, please make sure that:
In order to use the exchange, and returning proper quality goods, please make sure that:
- The item has not been used and has no signs of use: scratches, chips, scuffs.
- The software has not been altered, etc.
- The item is fully complete and intact in its packaging.
- All labels and factory markings are preserved.

FAQ
I'm sure that different crypto wallet apps and exchanges are on your laptop currently. Probably you've encrypted your hard drive and installed antivirus. But what if you are "asked" to turn on your device and show everything? In England, you can get three years in prison for refusing to do so. And if are these ordinary bandits? Options are few... . With our laptop, you don't have to worry about multiple iterations and work calmly with your crypto-currencies. In case when your laptop is lost or stolen, it is impossible to turn it on and figure out what was previously stored in it. Under coercion, you can always go into the wallet with the lowest balance - because no one will check your version of events.
The Tails flash drive has no hardware store files protection and can be hacked even in use - difficult but not impossible. Although the drivers set inside it are limited enough - no one will add drivers specifically for your laptop model - the Internet network may not work on your laptop model at all. Inside there is a very scarce set of software - without special knowledge, you cannot add new software to the assembly. At the same time, there is no hardware protection on Bios/camera/audio/USB - if Bios is hacked all OSs that are installed on the layer above will be under the hacker's control. As for Librem - it has a hard drive - the encrypted OS will not save from raiders or hackers. There is no Bios hardware protection, while the peripheral hardware protection is implemented by integration into the motherboard. The laptop is made in China, the government of which is a “supporter” of privacy and anonymity. The Kryptos Private Laptop has a separate module with hardware management of peripherals and Bios. This module is inserted using manual soldering and it is independent of the motherboard - so there is no access from the manufacturer.
Almost every device was already configured securely, and the user manual will be provided.
It is possible to hack everything - it's a matter of price/time/money. Who said that you haven't been hacked at the moment? After all, a hacker can wait for a couple of months to monitor your activity. If your laptop has a hard drive, then that means, it is possible it can be hacked. The antivirus helps very little - hackers are always a few steps ahead in technology and attack methods. We have been approached by traders asking us to check their Macbooks for viruses - large sums of money have been stolen and quite proficiently. It is impossible to hack a mechanical light switch – it is this ideology behind our Kryptos Private Laptop.
It's all a matter of understanding its value to you and in a habit. You can't harm yourself or your device by clicking on Trojan links and downloading unfamiliar files. We provide a step-by-step manual on how to use our products. It isn’t in the public domain not to give the opponents extra data.
No, the access to data from your devices does not go to any servers. We do not receive any data from you. We are always open to any audits at the expense of users about this issue.
Latest news
Order a service
Fill out the form and we'll get back to you soon
Contact us
Leave your details and we will answer your questions