Could we protect our privacy, and why Telegram won't definitely help? We sort it out with Yuri Melashchenko, information security expert and CEO of Security Services Group.
What's wrong with Telegram
The belief in the Telegram security is largely based on Pavel Durov's refusal to hand over the keys for the decryption of users' correspondence to the FSB.
However, the messenger does not encrypt messages by default, though even WhatsApp does this. The end-to-end encryption can be enabled manually and only in private chats.
"Regular and group chats are not protected by end-to-end encryption, which means Telegram sees your correspondence and saves them on servers. If you use this messenger, create "secret chats," enable the automatic deletion of correspondence, and prohibit taking the screenshots. But remember that even these restrictions can be bypassed with a second phone with a camera," Yury Melashchenko explains.
No one can guarantee that the content of regular chats will not fall into the hands of third parties. The code of Telegram's servers is closed: there is no way to check its security.
You can only create an account using a phone number. And this allows bad actors to intercept SMS to log into accounts and associate users with each other.
Messenger is popular because of its intuitive interface, and a large number of features. However, in terms of security and privacy, it has several worthy alternatives.
Five encrypted messengers
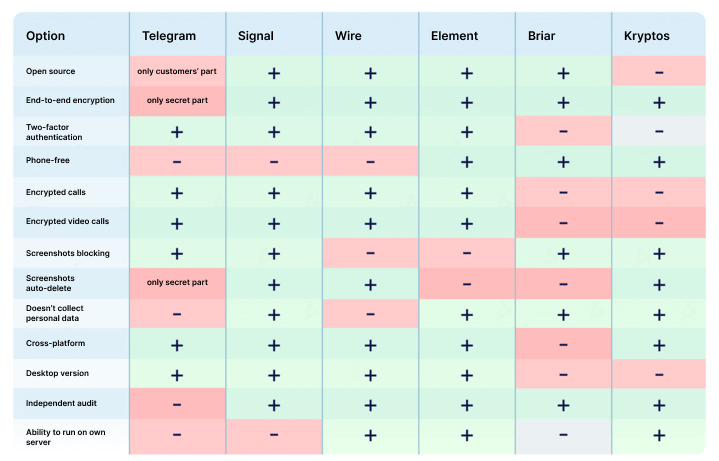
There are a lot of evaluation criteria. We chose the basic ones: free version, end-to-end encryption, open source, two-factor authentication, encrypted calls, and auto-delete messages.
"These are the basic parameters. In addition to them, the ability to deploy on their own server, resistance to “man-in-the-middle attack” and resistance to data obtained with Cellebrite UFED, Elcomsoft, and Oxygen Software are significant.
Such systems allow reading device data, including deleted files and correspondence. Just turn on-air mode and open a messenger: everything you can see there can be taken out," the CEO of Security Services Group comments.
In this article, we will consider five free messengers that meet all or most of the above criteria.
1. Signal is an open-source messenger by Open Whisper Systems. The project team created the protocol with the same name, which WhatsApp uses too.
In Signal, every chat or call is protected by end-to-end encryption. Users can configure auto-delete messages and pin-code login.
The service passed several third-party audits.
“Signal is considered the most secure messenger. But it also has weaknesses: you need to register by phone number and trust the server owner, who owns the encryption keys. We tried several times to deploy our own server, but the attempts were unsuccessful.
The messenger protects users better than Telegram: if a hacker intercepts the SMS, he will not get access to the correspondence history - it is not on the Signal servers. But it is stored on the device, so you should set a pin code to enter the application. And this will help protect data in case of guessing a password to a phone or computer," Yuri Melashchenko notes.
Platforms: iOS, Android, Windows, Mac, and Linux.
2. Wire is a messenger with end-to-end encryption, self-deleting messages, and open source.
The application developer is the Swiss company Wire Swiss, which focuses on the corporate market. However, they offer a free version of Wire Personal for individuals.
In order to create an account, personal information such as a phone number or email address is required. Wire was audited by Kudelski Security and X41 D-Sec.
Platforms: iOS, Android, Windows, Mac, Linux, and Web.
3. Element is an open source messenger with a decentralized structure. It uses the open standard Matrix developed by the British non-profit organization The Matrix.org Foundation.
The service allows you to create anonymous accounts and send messages to other messengers. In the app, all chats and calls are protected by end-to-end encryption.
Users can connect to existing servers and create their own. The latter can be a weakness if the server owner makes a mistake when setting up and further operation.
Platforms: Android, iOS, Windows, Mac, Linux, and Web.
4. Briar is an open-source code P2P messenger for Android. It uses the Tor network by default but sends messages via Wi-Fi or Bluetooth if there is no Internet connection.
Users can communicate in chats, private groups, and forums and write blogs. To register, you need to create a username and password.
You need to add contacts manually - using QR codes or invitation links. If you delete the application or forget the login data, you will lose access to your correspondence.
The weaknesses of Briar are the work only on one platform, high battery drain, and message delivery only when both users are online. Also, Briar does not allow you to add the same contacts via new links. All this indicates a centralized database.
Platforms: Android
5. Kryptos Private Messenger is a messenger with end-to-end encryption, anonymous registration, and private external links. It supports the "double-bottom" function when user can create two accounts and log into them with different passwords.
Kryptos Private Messenger server is not involved in key distribution. Messenger creates a key pair for each user and keeps it on his device in encrypted form. This approach makes it impossible to conduct “a man-in-the-middle attack”.
User correspondence is in RAM and automatically deleted when the application minimizes so that it cannot be read when physically accessing the phone or computer.
The messenger uses its own virtual keyboard and the Fortuna pseudorandom number generator created by Bruce Schneier and Niels Ferguson. It reads the gyroscope, timer, and user input in order to avoid potential vulnerabilities in the PRNG system.
"The virtual keyboard is an additional means of counteracting UFED devices. Built-in keyboards remember every word you have ever entered on your device. With access to your phone, it can get this vocabulary even if you wrote messages in a messenger with end-to-end encryption," the CEO of Security Services Group says.
Kryptos Private Messenger is at the initial stage of development: it supports text and voice messages, file sending, private chats, and groups.
Currently, the Kryptos team is looking for investments to create a project with a federated server system and private crypto-currency.
The developers plan to add call support to the messenger, finalize the interface and fully open the application code.
Platforms: iOS, Android, and Web.
General Digital Security Tips
- Download applications only from official store, and choose messengers with end-to-end encryption.
- Don't give any extra information about yourself: register accounts with virtual phone numbers and single-use mailboxes. If you use authentic information, make your profile available only to your contacts.
- If someone you don't know wrote to you, make sure you call them back to verify their identity.
- Don't click on links or download files, even if someone you know sent them. Ask over the phone or in another messenger if it was really him.
- Turn off sending email backups to the cloud - not all applications store them in encrypted form.
- Set a pin code or password to sign in to the messenger. Set up two-factor authentication if the application supports this function.
- Don't send sensitive information to messengers. You don't know whether your interlocutor deletes correspondence and whether third parties have access to it.
